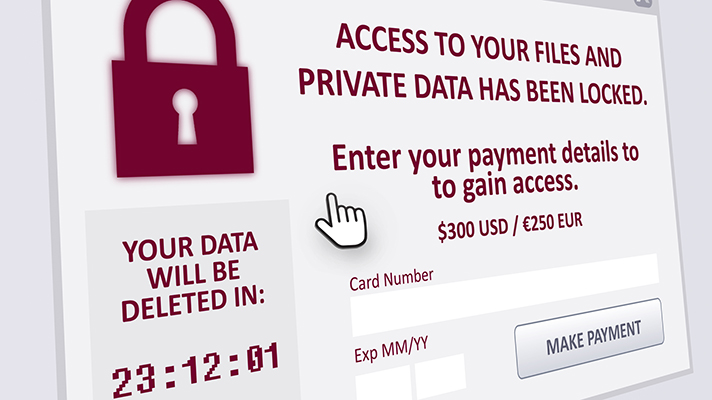
Recently the PSNI Cyber Crime Centre engaged with a Northern Ireland company that was the victim of a ransomware attack.
To help raise awareness of cyber crime in general and ransomware in particular, the victim agreed to share their experience with others.
As a company, how prepared did you feel your organisation was before this incident took place?
We had suffered from a smaller attack 18 months previous. We implemented additional measures (procedures and various new technologies) to combat the threat and believed we had sufficient protection in place.
But we have extensive legacy (older technology) systems which are harder to protect.
How did this incident impact on your ability to carry out day to day business?
For the first 4 working days over 70 – 80% of day to day business was impacted. It took 10 working days for the majority of day to day working for the core business to be restored. Smaller business operations took longer.
What advice would you provide a local organisation preparing for an event such as you experienced?
Change your mind set from “if it will happen” to “it is going to happen”.
Cyber security and Information security is a combination of having dedicated and skilled staff (internal & external), dedicated technologies and processes.
- Maintain your software with the latest upgrades and patches.
- Consider the adoption of Cloud technologies. These vendors have vastly more capability to protect your systems.
- Have an incident response plan / partner.
- Have each department create a business continuity plan
i.e. how could our department survive without business systems for x days?
What have you learned from this experience?
Mostly that Cyber security is an ongoing and evolving threat that needs a bigger percentage of the business focus.
- Implement absolute information security procedures for access and control – even if that slows down business innovation.
- Accelerate the removal of older legacy systems.
- Implement IT info & cyber security best practice and without exception.
- Dedicate more resources to information security.
Why not just pay the ransom?
We had excellent backup and recovery systems so we had the ability to recover 99% of all information.
Also we would fear paying the ransom would encourage further attacks or raise our profile as a soft target for Cyber Criminals.
What cost would you place on the impact this incident had on your organisation?
Well into six figures.
This company already had experience of one cyber attack. It had made preparations for another and yet it still fell victim to one.
It is unlikely that you can ever be totally secure, but you can make it harder for the criminal and you can mitigate the risk.
Training and staff awareness are an essential element in preventing cyber crime.
A ransomware attack is just one way in which you might be exploited.
So much of cyber crime relies on exploiting trust ( Fraud – It started with a Tweet ).
Security is a process and a frame of mind. It is never just a tick box exercise.
Where can I turn for help?
There is an array of resources out their to help individuals and organisations plan their response.
A good place to start is the Northern Ireland Cyber Security Centre (Twitter @NICyberSC) or the National Cyber Security Centre (Twitter @ncsc or @cyberawaregov).
You can follow the PSNI Cyber crime team on Twitter @PSNIBelfast.
The NCSC has provided a really useful range of Infographics that link to more detailed guidance..